Cyberattack on municipal IT service provider: a detailed analysis

- Cyberattack on municipal IT service provider: a detailed analysis
- The impact of the cyberattack on the IT service provider Südwestfalen-IT (SIT)
- IT outsourcing: opportunities and risks in the context of cyber security
- Opportunities and challenges of IT outsourcing
- Cyber security in the context of IT outsourcing
- The impact of the attack and how municipalities are responding
- Measures to strengthen IT security: Lessons from the cyber attack on South Westphalia IT
- Conclusion
- Further links
In today's digitalized world, cyber attacks are a constantly growing threat that does not stop at municipalities. One recent example is the far-reaching attack on the IT service provider Südwestfalen-IT (SIT) in North Rhine-Westphalia, which affected over 70 local authorities and led to considerable disruption to various services.
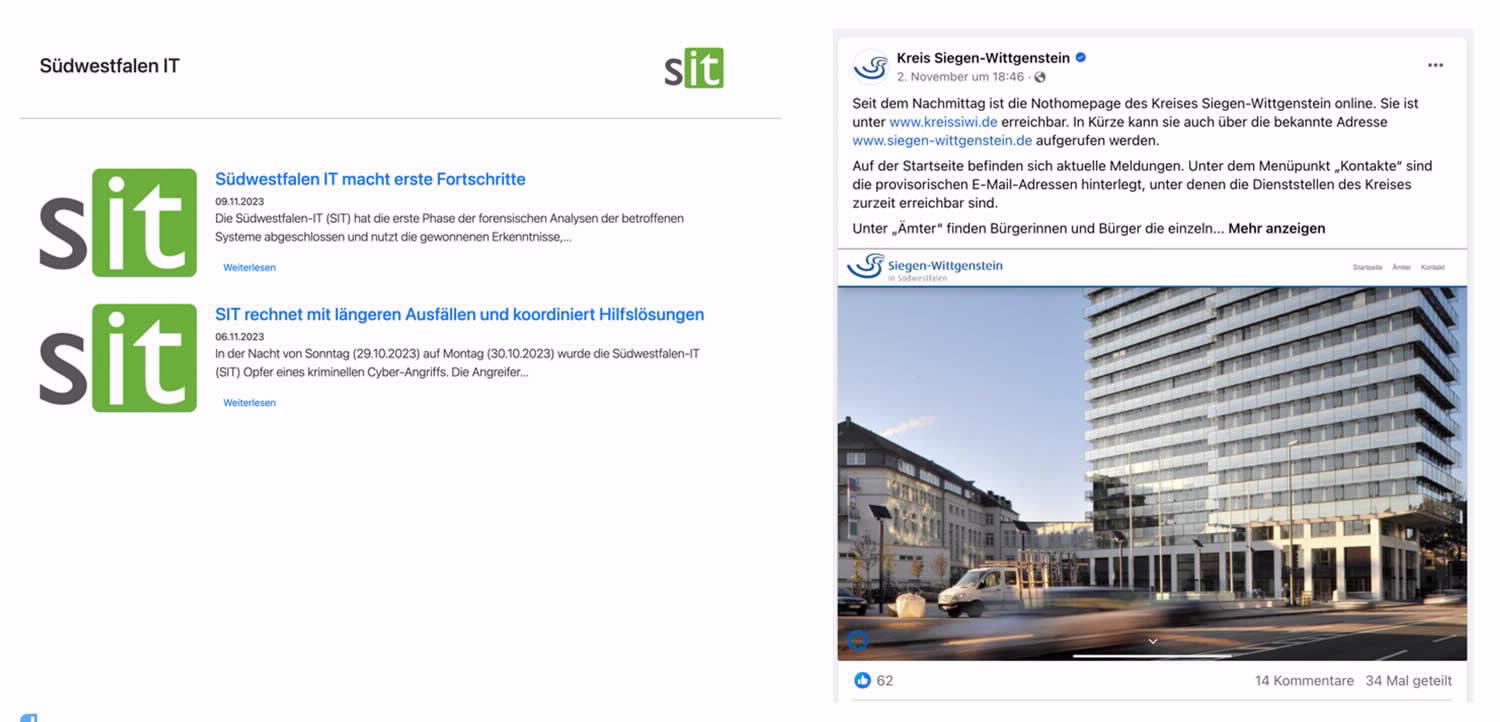
The impact of the cyberattack on the IT service provider Südwestfalen-IT (SIT)
Akira ransomware has been identified as the culprit behind the attack on SIT's systems. To prevent further spread of the malware, all connections of the data center to and from all affected municipalities were cut.
As a result, the administrations no longer had access to the specialist processes and infrastructures provided by SIT, which led to considerable restrictions in their services. The municipalities affected, mainly in South and East Westphalia and to some extent in the Ruhr region, were left without functioning websites or digital services..
An increasingly common problem: cyber attacks on municipalities
This incident is not an isolated case. In 2022, 27 municipalities in Germany fell victim to cyber attacks, which shows that cities and authorities are increasingly becoming the focus of cyber criminals. Federal Minister of the Interior Nancy Faeser emphasizes the importance of preparing for cyber attacks and prioritizing cyber security. See also the new IT security situation report 2023 from the BSI here
IT outsourcing: opportunities and risks in the context of cyber security
In the digital era, IT outsourcing is a widespread phenomenon that offers companies and local authorities numerous advantages. From cost efficiency and access to specialized expertise to lean administrative structures, the appeal of outsourcing is undisputed. However, the incident at Südwestfalen-IT impressively demonstrates that it also harbors risks, particularly in terms of IT security.
Opportunities and challenges of IT outsourcing
Advantages of IT outsourcing:
- Cost efficiency: Significant savings can be achieved by using the low-wage sector and locating data centers in low-cost areas
- Lean administrative structures: Outsourcing providers can often ensure more efficient administrative structures
- Adherence to schedules: The contractual obligation to adhere to schedules can improve project management efficiency
- Efficient software licensing and hardware purchasing: Outsourcing providers can better control these aspects thanks to their industry knowledge
The challenges of IT outsourcing:
- Loss of control: Maintaining control over outsourced tasks can be a challenge.
- Dependence on the provider: A failure of the service provider can have far-reaching consequences.
- Security risks: Data leaks or losses are potential risks when outsourcing IT tasks.
Cyber security in the context of IT outsourcing
The cyber attack on Südwestfalen-IT underlines the urgent need for companies and local authorities to be vigilant in order to quickly detect and respond to cyber attacks. It is not only the company's own cyber security that plays a role here, but also that of the IT service provider. It is therefore crucial to implement robust cyber security measures both within your own organization and at service provider level.
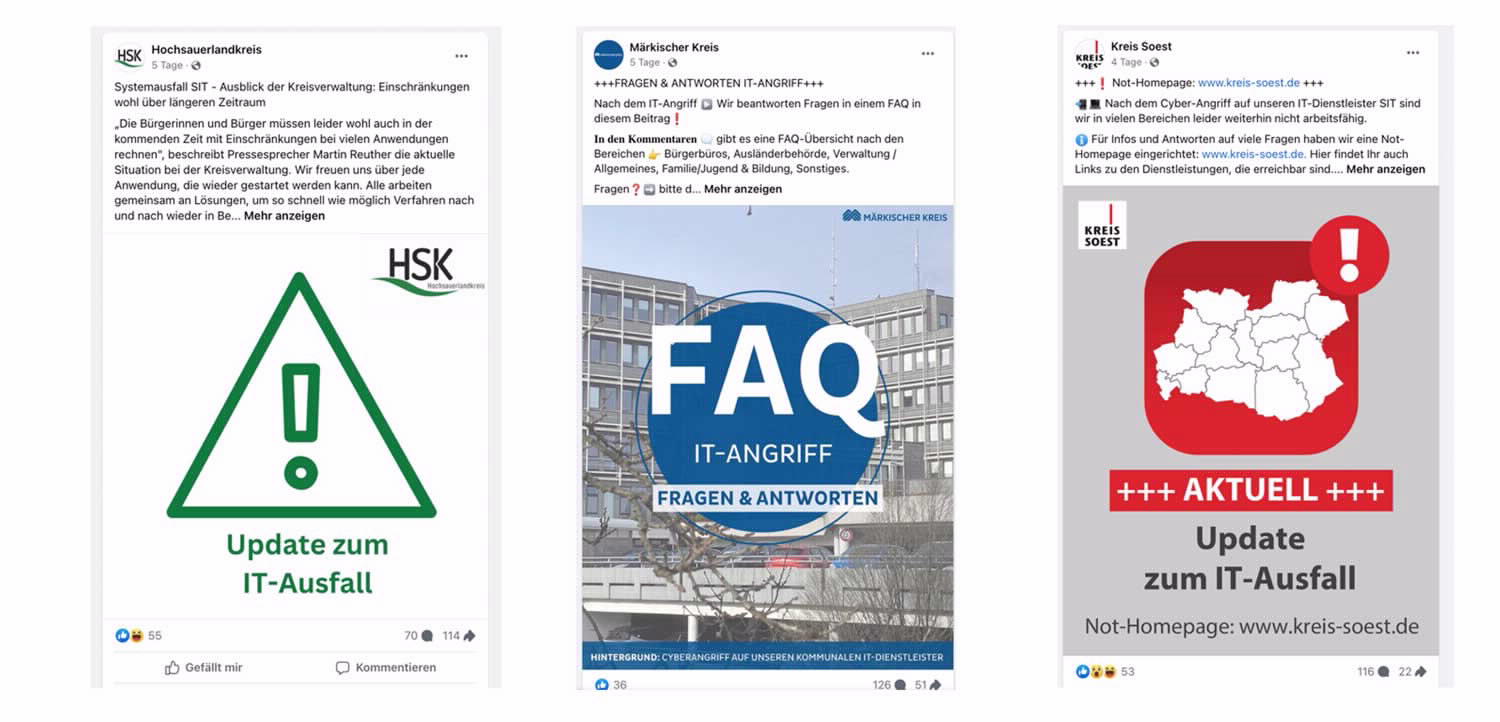
The impact of the attack and how municipalities are responding
The impact of the cyberattack was far-reaching and affected a wide range of services, from issuing new passports and vehicle registrations to certificates from the registry office. Many employees had to resort to pen and paper to process inquiries.
Temporary measures have been introduced in some municipalities, such as temporary forms, communication via social media and an emergency website to provide essential services until systems are restored.
Sources:
- Hochsauerlandkreis - informed via Facebook (you will be redirected to an external page)
- Märkischer Kreis - informed via Facebook (you will be redirected to an external page)
- Siegen-Wittgenstein/Olpe - informed via emergency homepage kreissiwi.de (you will be redirected to an external page)
- Soest - informed via Facebook (you will be redirected to an external page)
- Lüdenscheid - informed via emergency homepage www.luedenscheid.de (you will be redirected to an external page)
Measures to strengthen IT security: Lessons from the cyber attack on South Westphalia IT
Extended Detection and Response (XDR) and Endpoint Detection and Response (EDR)
A solution such as Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR) would most likely have detected unusual activity and raised the alarm before the ransomware could take full effect. EDR provides continuous monitoring and analysis of endpoint activity and can alert on unusual behavior patterns, such as unusual file access or changes to system files. In addition, XDR and EDR offer solutions for remediating security breaches, enabling immediate action in the event of an attack.
More about endpoint security here
Network segmentation as a protective measure
Effective network segmentation might have prevented or at least limited the spread of the ransomware within SIT's network. Each segment acts as an independent network and an infection in one segment could be isolated and contained without spreading to other segments.
Network segmentation also provides an additional level of protection by strictly controlling communication between segments. This means that even if an attacker gains access to one segment, access to other segments is not automatically granted. This makes the attacker's job more difficult and increases the likelihood that the attack will be detected before it can cause major damage.
More on the topic of network segmentation here
Reducing the impact of cyberattacks through Visibility-as-a-Service (VaaS)
In-depth insights into the IT infrastructure
VaaS provides a comprehensive insight into an organization's IT infrastructure. Using specialized scans and tools, VaaS performs detailed checks on firewall gateways and management systems. In the context of the attack on SIT, VaaS could have identified potential vulnerabilities or hardware issues before the cyberattack took place. This would have paved the way for preventative measures to either prevent the attack or minimize its impact.
Compliance with IT laws
Compliance with IT legislation such as NIS-2 is essential for many organizations. Non-compliance can lead to significant fines. VaaS assists in achieving the primary security objectives - confidentiality, integrity and availability of networks - and thus helps to meet legal requirements.
Network analysis and firewall rule analysis
VaaS identifies security risks in existing IT components and in the entire network through comprehensive network analysis. This enables security gaps to be closed, increases network security and protects data from threats, intruders and other security risks.
The VaaS firewall rule analysis includes a thorough examination of the firewall rules, general settings, system patch statuses and other module configurations. Based on the results of the analysis, recommendations are made for optimizing the rules and the existing high-availability environment.
At SIT, such an analysis and optimization of the firewall rules might have helped to ward off the cyberattack or at least limit its spread.
External Security Operations Center (SOC)
By using an external Security Operations Center (SOC), organizations can benefit from a comprehensive managed security service. The SOC experts monitor the infrastructure around the clock, proactively detect and respond to security incidents, analyze threats and implement incident response measures. This ensures the protection of systems and data against current and future attacks.
In the case of the cyberattack on SIT, a SOC might have detected the attack at an early stage and initiated countermeasures to minimize the impact.
More about VaaS here
The importance of a well-structured IT contingency plan
A well-structured and regularly practiced IT contingency plan could have a significant impact on minimizing the impact of a cyberattack. Through clear responsibilities, risk assessment, contact details, recovery plans, security policies and regular audits, this plan could help reduce the downtime and costs caused by a cyber attack.
Emergency procedure and responsibilities
A clearly defined emergency plan provides a step-by-step guide for employees to respond correctly and efficiently to attacks. It also defines responsibilities so that every employee knows exactly what to do in such a situation. This could help to avoid panic and chaos.
Risk assessment and management
By conducting a risk assessment, potential vulnerabilities in the systems could have been identified and measures taken to address them before they were exploited by attackers.
Contact list and external service providers
A contact list with the contact details of the relevant internal and external persons is invaluable in crisis situations. It makes it possible to react quickly to the incident and inform the right people to start the recovery as soon as possible.
Disaster Recovery Plan (DRP)
A DRP would describe the recovery process after the attack and include strategies for recovering data. This could help to minimize downtime and resume operations as quickly as possible.
Security guidelines
The implementation of security guidelines could have prevented further attacks and reduced the spread of the damage.
Audits & tests
Regular reviews and testing of systems and processes are critical to ensure they are compliant and secure.
Employee training
After all, regular training for employees could have prepared them for possible emergency scenarios. This could have helped them to be able to react quickly and efficiently to the attack.
Conclusion
Overall, the Südwestfalen-IT case shows the urgent need for robust cyber security measures, both within organizations and at IT service providers. By implementing network segmentation, XDR or EDR, VaaS and well-structured IT contingency plans, companies and municipalities can strengthen their resilience against cyber attacks and be better prepared for such incidents - true to the motto: prevention is better than reaction. 😉
Further links
More on the topic of network segmentation
More about Visibility-as-a-Service (VaaS), network analysis, firewall rule analysis,....
https://www.bristol.de/leistungen/careforce-one/
More about endpoint security
https://www.bristol.de/wie-modernes-endpoint-security-management-funktioniert/
