Contents
TISAX® - Increasing IT securityin the automotive industry supply chain
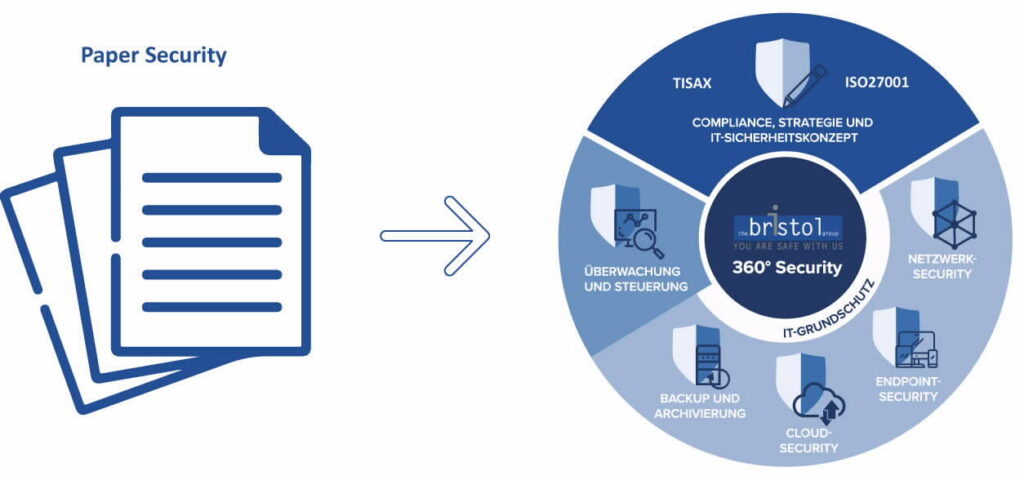
Holistic operational approach instead of just paper security
The security of information and information systems is of crucial importance for the smooth running of business processes. As a central task of company management, information security plays an important role in ensuring the secure flow of information. However, with regard to networking and globalization in the automotive industry, the risks are also increasing, both internally and externally. In order to counteract these risks, it is necessary to establish suitable protective measures.
The German Association of the Automotive Industry (VDA) has developed the VDA Information Security Assessment (ISA) catalog in collaboration with industry experts. This industry standard provides companies involved in the automotive industry's value chain with recommendations and assistance for implementing information security.
An important component of the VDA ISA catalog is the TISAX® (Trusted Information Security Assessment Exchange) standard. This standardized proof of security enables companies to demonstrate their security measures along the supply chain and thus gain the trust of their customers.
Why, why, why do I need TISAX® at all?
The TISAX® standard is primarily aimed at suppliers in the automotive sector (or industry). Companies operating in this sector are faced with increasingly complex supply chains and growing requirements in terms of information security. Compliance with the TISAX® standard enables companies to take their information security obligations seriously and thus protect trade secrets. TISAX® serves as a tool for measuring and verifying information security along the entire supply chain.
Why is the TISAX certification useful?
TISAX® certification is proof of security in the supply chain. Proof of compliance with the TISAX® standard is an important step for companies to gain the trust of their clients and strengthen their position as a reliable partner in the automotive industry. The certification shows that the company has implemented effective security measures and is continuously developing its information security.
The path to TISAX certification
TISAX® certification requires extensive preparations and the fulfillment of certain requirements. Companies must analyze their information security measures, identify weaknesses and implement suitable measures for improvement (technical and organizational measures in accordance with the GDPR). Successful certification requires comprehensive documentation of the implemented security processes and measures.
The effectiveness of TISAX certification
TISAX® certification goes beyond meeting security requirements on paper (paper security). It ensures that companies actually implement effective security measures to guarantee their information security. Certification enables companies to gain the trust of their clients and position themselves as trustworthy partners.
Insider knowledge: We have found that many companies have TISAX certification on paper but do not meet the organizational or technical requirements of the certification. We call this paper security.
Our offer for TISAX
- We support you in implementing a TISAX organizational structure and the necessary technologies.
- We protect your company holistically through analyses, security training and the establishment of a secure network.
- Our network analysis includes capacity checks, network separation, firewall configuration, IDS and SIEM implementation and Visibility-as-a-Service (VaaS).
- We improve the communication and security of your supply chain.
Our solution: Much more than TISAX Paper Security
We help companies to not only meet the requirements of the TISAX® standard on paper, but also to actually implement effective security measures. With a holistic analysis and the creation of resilience, we ensure that your company is comprehensively protected and meets the increasingly stringent requirements.