Guardians of the Enterprise - ARP-GUARD

Introduction
In a world ruled by data streams and algorithms, the company GlobalData* stands as an impregnable fortress. In the depths of its servers, explosive information is stored, coveted by unscrupulous actors and curious hackers. These are countered by powerful protection mechanisms and vigilant employees.
In the shadows of this data-driven world, beyond the reach of flashing lights and security systems, two skillful individuals are at work. They are hackers, modern knights of the digital age, driven by a thirst for adventure and the thrill of the impossible. They have set themselves the goal of hacking GlobalData and stealing its sensitive information. Their names are Nightfox and Specter.
The first advance
As night falls, Nightfox and Specter put their plan into action. Their fingers dance across the keyboards, a silent prelude to the approaching storm. Screens flicker before them, gateways to a world they intend to conquer. The first attack is carefully planned, a precise strike against the outer defenses of the GlobalData fortress. The first encounter turns out to be a gatekeeper who seems to recognize every intruder and proudly bears the inscription ARP-GUARD on his chest.
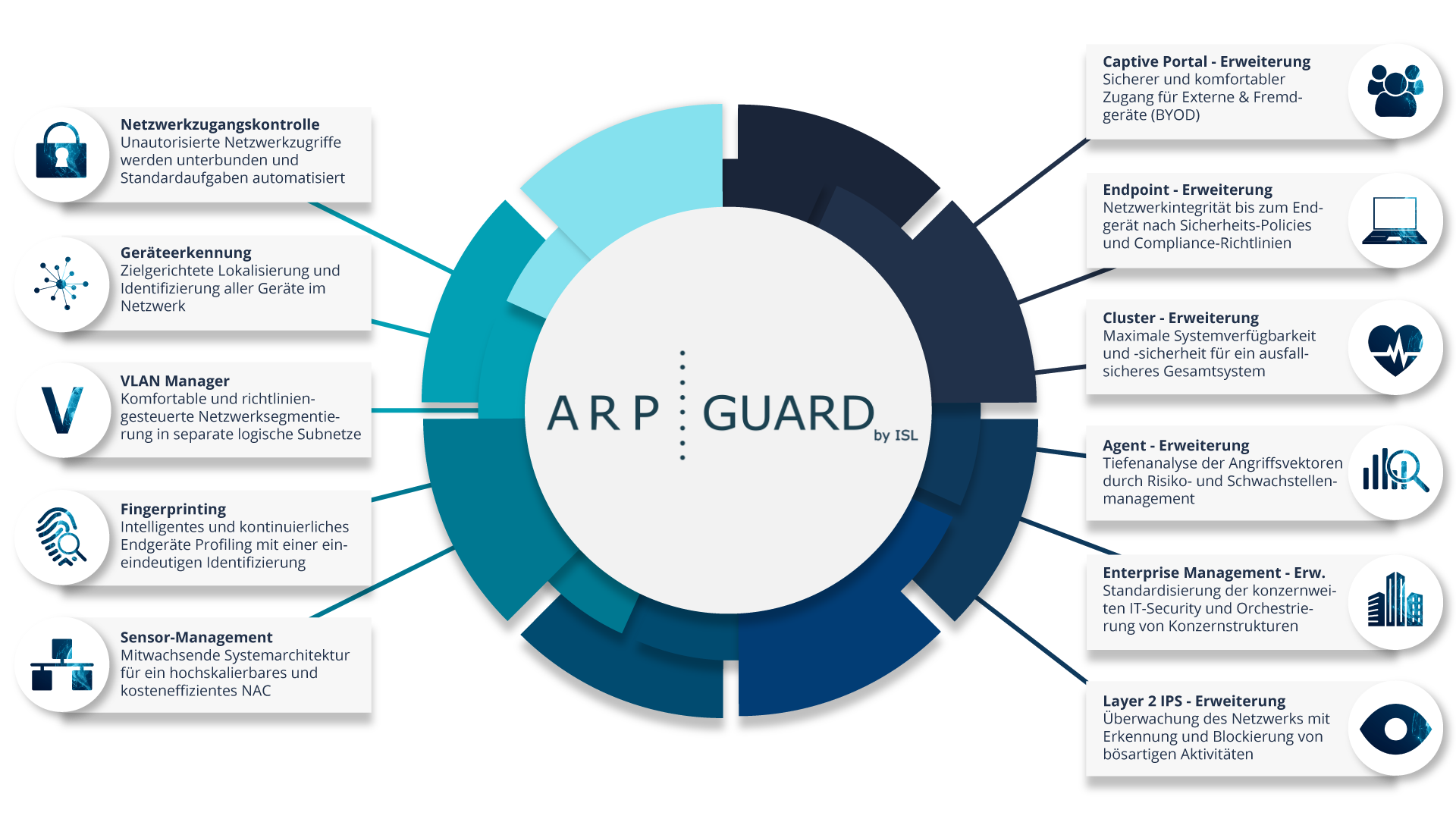
ARP-GUARD - Network Access Control
The hacker duo is determined to cleverly trick the guards. Using fake digital identities and the art of digital infiltration, they try to pass themselves off as harmless employees. But ARP-GUARD NAC is the ultimate gatekeeper, whose job it is to protect the network from uninvited guests by checking every user and every device before they are allowed to penetrate any further. This attempt backfired and the gates for Nightfox and Specter remained closed.

The hidden path
After Nightfox and Specter are pushed back by the steadfast ARP-GUARD, they search for a hidden path, a less guarded entrance into the digital realm. Their first defeat has sharpened their senses, and driven by an insatiable thirst for knowledge, they finally discover a small, barely visible loophole in the digital wall - a way to bypass the strict controls of Network Access Control.
However, what they hope will be a simple passageway quickly turns out to be a complex labyrinth of security measures hidden behind the illusion of simplicity. An invisible net stretches across the endpoints, a guardian that not only guards the gates but also enforces the laws and rules of every individual in the company. Any attempt to circumvent the system is immediately detected and blocked. Weak endpoints are immediately sent to quarantine so as not to jeopardize the security of the fortress. The Captive Portal guest access appears to be a loophole - but the attempted attack ends in the quarantine VLAN.
The search for allies
When Nightfox and Specter fail against the seemingly insurmountable protection mechanisms of the digital fortress, they are forced to rethink their tactics and look for new approaches. Their journey leads them to a secret meeting, a Conclave of Shadows, where the brightest minds of the underground hacker scene come together. Among them is a legend known only as Shadow, a hacker whose skills and successes are almost mythical.
ARP-GUARD VLAN Manager
With a mixture of awe and curiosity, they listen to Shadow's tales of his encounters with the ARP-GUARD VLAN Manager, the control and failure center of the digital fortress, which even resourceful hackers cannot gain access to.
The cluster's server replication ensures that any loss is immediately replaced, a phoenix from the ashes that re-forms from every attack. Nightfox and Specter stand in awe of this technology, which not only protects the digital kingdom but also makes it immortal.

The Code of the Guardians
In the dim glow of the monitors, surrounded by the muffled voices of the hackers, Nightfox and Specter experience a silent revelation. The words of Shadow, the master of the unseen paths, echo in their minds, revealing the truth about the fortress they once tried to topple. The stories of its impregnable defenses shake their convictions.
Driven by a mixture of awe and rekindled curiosity, Nightfox and Specter make a decision that will change their destiny forever. They decide to stop fighting the fortress and use their knowledge and skills to strengthen the walls they once tried to bring down. In doing so, they realize that true greatness lies not in destroying, but in creating and improving.
After an intensive year of training under the guidance of the BRISTOL GROUP, the knightly order of cyber security, the former shadow walkers blossom into true masters of their trade. They learn the language of the guardians, the rituals of ARP-GUARD fingerprinting and the secrets of the ARP-GUARD VLAN Manager.
The world of IT security begins to whisper their names, not as a warning, but as a banner of excellence. Nightfox and Specter become sought-after experts whose advice and skills are in demand. Their previous attacks now serve as lessons, their cunning as the basis for stronger defenses.
When they finally return to the gates of GlobalData, they do so not as intruders, but as guardians. The walls that once seemed impenetrable welcome them as part of their structure.

Epilogue
The gripping short story of Nightfox and Specter, the former digital outlaws turned cybersecurity guardians, reflects a deep understanding of the challenges of the Zero Trust approach. This security philosophy, which views all network participants as potentially dangerous and requires constant verification, presents a complex challenge that no organization can ignore. The NIS-2 directive also calls for zero-trust principles. Read here
The introduction of ARP-GUARD as a Network Access Control (NAC) solution offers a robust answer here. It serves as a bulwark against unauthorized access and is a prime example of how modern technology can bridge the gap between theory and practice. With ARP-GUARD, organizations can exercise fine-grained control over all network access, improve compliance and ensure end-to-end monitoring.
The end of Nightfox and Specter's story is therefore more than just a narrative: it is a real-world example of how in-depth expertise and the right tools - in this case ARP-GUARD - can help to implement the principles of Zero Trust and thus strengthen an organization's security architecture in the long term.
*The plot and all characters are fictitious. Any resemblance to living or real persons is purely coincidental.
