
Network segmentation - IT security part 2
After explaining the basics of network segmentation in the first part, we would like to go into more technical depth in the second part. To do this, we have invited our security expert Nox. Nox has been familiar with the BSI IT-Grundschutz building blocks for some time. During the time in the home office, Nox had time to deal with the topic "NET - Networks and Communication". The trainee Paul is just as interested in this topic and seeks a discussion with Nox.
BSI Basic Protection NET.1.1: Network architecture and design
Nox considers NET.1.1 to be particularly interesting for network segmentation:
"To ensure a high level of security, additional security-relevant aspects must be taken into account. Examples of this are the secure separation of different clients and device groups at network level and the control of their communication using firewall technology. Another important security element, especially in the client area, is network access control."
Paul has heard this before and hangs on Nox's every word.
This goes into further detail. The BSI calls for the strict separation of clients and servers, see requirement NET.1.1.A5 Client-server segmentation: "Clients and servers must be placed in different security segments. Communication between these segments must be controlled by at least one firewall." It is also recommended to further subdivide the network into security segments based on the protection requirements of the IT systems. Nox pulls out a pen and diagrams the segmentation.
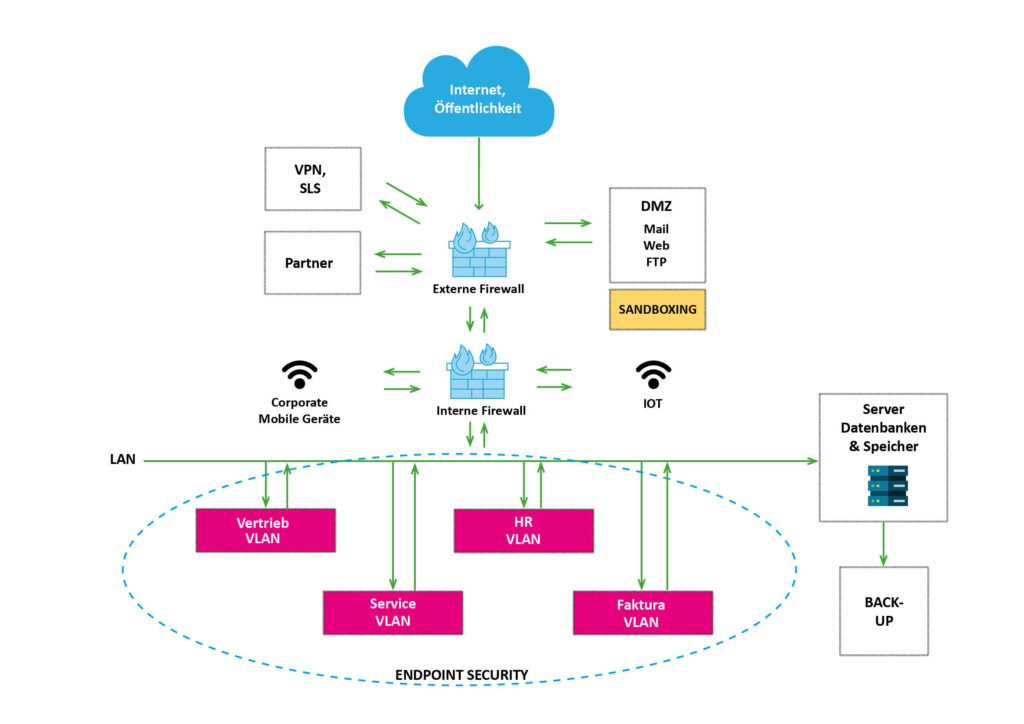
The result is a separation of different groups in the network by means of VLANs, for example. The transitions between the segments (security zones) created in this way are usually formed by firewalls that can control incoming and outgoing traffic.
Paul only understands what's going on, so Nox takes another step back.
In line with the topic - Upcoming webinars on cyber security
| Date | Event | Format | Details |
|---|---|---|---|
| 28.11.2024 | Identify IT risks in accordance with NIS-2 | Online | More info |
| Aufzeichnung erhalten | Overview of key performance indicators (KPIs) in cyber security | Online | More info |
| Aufzeichnung erhalten | FortiPAM- Privileged Access Management, ZeroTrust and MFA | Online | More info |
| Aufzeichnung erhalten | Features and benefits with Check Point SASE | Online | More info |
The basics of network segmentation
Segmentation involves literally building doors and walls into the company network. From a technical point of view, the entire network is divided into individual network segments, i.e. IP subnets. For technical and organizational reasons, this can result in a large number of segments, but it is not necessary to clarify the protection requirements for each one individually. Criteria can be, for example, whether the systems contained are directly connected to the Internet, whether the devices are directly accessible to users or whether even uncontrollable third-party devices can be placed in the segment.
Which network zones can be segmented across the board?
However, the most important stereotypes and basic ideas should be mentioned:
"Trusted" zones:
These are zones in which only managed devices with a known configuration and known health status can be found. An example would be a well-protected client network. Shown in magenta in our graphic. This zone type implicitly guarantees that there is no danger to the users of the zone from third-party devices. This is easy to guarantee for network segments that contain servers/services. The only interface is the zone transition at the firewall. All systems in it are provided and operated by administrators. Client network segments, on the other hand, are a challenge. On the one hand, there are users behind the clients, who can get up to mischief with their end devices out of ignorance or intent if the protection configuration is inadequate. On the other hand, network ports and WLAN access points are often accessible to third parties (customers, passers-by, suppliers) or even the public. The following therefore applies to trustworthy zones: in addition to a well thought-out firewall rule set, access to the network should also be implemented using a network access control (NAC) solution. This protects the transitions. These so-called endpoint clients are further protected by endpoint security. (See here), which makes it largely impossible to misuse the end devices.
"DMZ" zones:
These are zones that enable exchange with the Internet in a controlled manner in order to provide services such as e-mail, web access, authentication (federation), etc. These zones are exposed to the Internet. Care should be taken to ensure that the systems in these zones are protected as far as possible at network level, i.e. the systems are located behind a perimeter firewall (external firewall), which only allows access to the most necessary IPs and ports. A common misunderstanding should also be mentioned: DMZs allow access from the Internet, but access directly to the medium (plugging in an end device) is not permitted at any time. In terms of network technology, these are specially encapsulated zones in which no user end devices can be found. They are only protected at network level and by a firewall.
"Management" zones:
They only contain systems that are used to provide and manage the IT infrastructure and are only used by privileged administrators. The systems in them should always be regarded as extremely sensitive, as they can be used to control the IT infrastructure. The basic rule when creating the zone matrix and implementing the firewall rules is: access from management zones to various zones is permitted (source), but access to management zones (destination) should be avoided as far as possible. Media access from the access area is strictly prohibited.
It is important that all systems within the zone have similar protection requirements. The system with the highest requirements is the yardstick and pace-setter.
Learning and implementing network segmentation?
Find out how to implement network segmentation in your own company in our practical workshop! Our long-standing IT security experts will show you how to do this using practical examples.

What does microsegmentation mean?
This makes sense to Paul and he asks how communication is secured within the large segments?
Experience has shown that communication at network level is often not restricted any further and this is precisely where an interesting problem lies.
Let's take the example of strict client and server segmentation outlined above. The servers are thus protected from unauthorized access by clients to a certain extent. Let's also assume that the servers that process particularly critical data are separated in an additional security segment of their own for the high protection requirements. At first glance, this appears to be a reasonable solution that can be set up once and then provide a solid level of security.
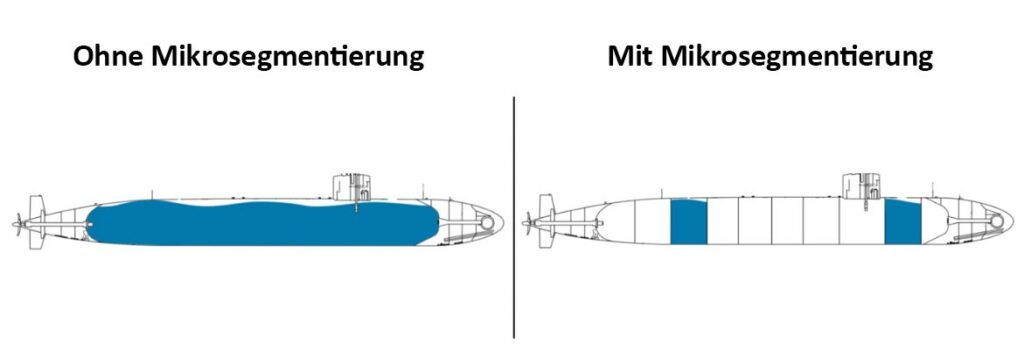
Unfortunately, there is also the extremely dynamic world of vulnerabilities. It may well be that certain servers (perhaps even servers with high protection requirements) are considered insecure because, for example, the operating systems cannot be patched in a regulated manner (or not at all) due to the running applications or the applications themselves have vulnerabilities that cannot be eliminated in the foreseeable future. These servers then naturally pose a fundamental threat.
Vulnerabilities could be exploited by an attacker to compromise the affected systems and steal or manipulate data or to attack other servers from this attack base.
End device segmentation in the internal network
The BSI IT-Grundschutz compendium then logically states in requirement NET.1.1.A6 End device segmentation in the internal network: "Only end devices that correspond to a similar security level may be positioned in a security segment."
The answer to this is clear: using the means of network segmentation, another security segment is set up as a cage in which insecure systems (in our example, IOT devices) are stored. Here, for example, all voice assistants, live cameras, ... are packed into separate networks. Traffic to and from the cage can then be precisely controlled, e.g. using a particularly strict set of rules and intrusion prevention techniques.
With the means of micro-segmentation, for example, such targeted protection of VMs could be created as required by using the distributed firewall. This solution is also interesting here because the distributed firewall is transparent for the network and the system would not have to be moved to another security segment in terms of network technology.
Network segmentation from an IT security perspective is a dynamic process
In practice, it has been shown time and again that network segmentation must always take into account the handling of insecure systems and is therefore never static in nature. Without a concept for the structure of poison cabinets and how to deal with them, network segmentation is not particularly useful. Network segmentation must therefore be able to react dynamically and quickly enough to new vulnerabilities in the systems and flexibly create additional protection for affected systems. If this protection is no longer required (perhaps because a patch has eliminated the vulnerabilities), it must also be possible to remove it just as flexibly. The protection must therefore be as close as possible to the affected end devices and be transparent for layer 3. Traditional network segmentation based on VLANs cannot achieve this and SDN-based solutions will increasingly close this gap.
Further links
BSI Basic Protection NET 1.1 - Click here
Peter, IT manager, and network segmentation - Part 1 - Click here
